
This article originally appeared in the May/June 2018 issue of Museum magazine.
In late 2016, the ride-sharing service giant Uber suffered a data breach that potentially exposed the personal information of 57 million Uber users and drivers. The company paid the hackers $100,000 to keep the data breach secret.
In mid-2017, an on-campus data breach connected to the University of Oklahoma’s file-sharing system unintentionally exposed educational records, dating back at least 15 years, through incorrect privacy settings. The file-sharing service was shut down indefinitely.
These are not isolated examples. Data breaches and cyber attacks in November 2017 alone resulted in 59 million records leaked worldwide, according to IT Governance Blog. The takeaway isn’t complex: all institutions need to invest in cybersecurity. Knowledge of the risks is key to developing the right approach.
Skip over related stories to continue reading articleAt every museum, information and communications technology (ICT) teams need to work closely with the executive team to identify vulnerable or mission-critical data, explain and work through risks and mitigations, and then develop policies and focus expenditure where it is most needed. The benefits of developing a museum-wide approach to cybersecurity include smoother compliance reporting, reduced insurance premiums, reputational assurance, protected revenue streams, and, most important, peaceful sleep as the servers hum and blink untroubled throughout the night.
Core Characteristics of Data Security
Three key characteristics of data security are confidentiality, integrity, and availability, known as the CIA triad. Together they describe a baseline standard for evaluating and implementing data security in any system or organization.
Confidentiality ensures that data is protected from disclosure to unauthorized parties. Confidentiality recognizes that data has a value: personal information, credit card numbers, trade secrets, government information. A key method of protecting data confidentiality is encryption. A common example is using the SSL and TLS cryptographic protocols for communications over the internet.
Integrity means maintaining the consistency, accuracy, and trustworthiness of data over its entire life cycle. Data must not be vulnerable in transit or at rest. Safeguards must also be in place to detect changes in data resulting from adverse events, such as electromagnetic pulses or a server crash.
Availability is the process of ensuring that data is available to end users and applications when and where they need it, in situations ranging from normal to disastrous. It includes necessary ICT procedures and tools to enable and continuously manage data to ensure its ongoing availability.
Approaches to Cybersecurity Threats
Cybersecurity threats fall into three main categories: external, internal, and hidden. Each requires its own approach to maintaining the CIA triad.
Boundary firewalls and gateways secure the digital boundary between the internet and a museum’s network. They provide a basic level of data protection by filtering network traffic to identify and block unwanted and potentially harmful information. This is an approach to managing external threats.
Staff are likely to pose the biggest internal cyber threat, though data breaches caused by staff are usually unintentional rather than malicious. Risks can be mitigated by configuring computers and software to provide access only to applications required for a particular role, mandating the use of strong passwords with regular cycles for change, and educating staff about what to do and not do so they become a “human firewall.”
Hidden threats may lurk in trusted software that has become outdated. By committing to current hardware, operating systems, and software, vendors will continue to provide support. When necessary, vendors release patches, which are additional pieces of software that fix security vulnerabilities or operational issues. Regularly applying patches reduces the risk of unauthorized access to data.
Planning for the Worst
Ransomware damage costs were estimated at $325 million in 2015, rising to $1 billion in 2016 and $5 billion in 2017, according to the research firm Cybersecurity Ventures. Costs included business disruption, data loss, reduced revenue, damaged equipment, and forensic investigation.
Organizations need an ICT disaster recovery plan, which describes how they will recover ICT infrastructure in the event of any disaster, including a cyber attack, that compromises the availability of technology. The purpose of such a plan is to recover the digital systems and infrastructure that support business processes critical to the museum’s operation. An ICT disaster recovery plan might include:
- A list of people on the emergency response team
- Procedures for declaring a disaster
- Procedures for invoking the disaster recovery plan
- Emergency communication methods and contact details
- Process to carry out basic recovery plans
- Viable alternatives to functions and services
- Process to retrieve data from alternative storage
- Training methods for emergency response team members
- Schedule for regularly testing the plan
- Any disaster recovery test or event should be followed by honest and exhaustive discussion of lessons learned, with the results folded back into the plan.
Developing a Cybersecurity Strategy
Systematically assessing and addressing the security risks specific to your museum can help minimize the likelihood and consequences of cyber attacks. That means ICT personnel and museum leadership need to understand each other. Consider using the five questions below to shape a fruitful discussion that leads to a strong cybersecurity strategy.
1. What would a serious cybersecurity incident cost our museum? If member records, financial data, or intellectual property were stolen, how quickly could you determine what was lost? Effective cybersecurity can avoid the direct costs of a cleanup and the indirect costs such as downtime, lost productivity, and loss of public confidence.
2. Who would benefit from having access to our information? Identify critical information essential to the ongoing function of your museum. This assessment will enable you to apply appropriate resources to protecting your data: highest-level protection for collection and financial data, lower security for ephemeral communications.
3. What makes our museum secure against threats? Cybersecurity is an ongoing process, not a product. As cyber attacks become more sophisticated and targeted, so do security techniques. To secure your museum, put in place appropriate security governance, clearly defined policy, user education, and third-party assessments, along with ongoing reviews.
4. How is staff behavior affecting the security culture? One malicious email attachment inadvertently opened by an unsuspecting staff member can potentially compromise your whole data network. Effectively trained staff enable a strong security culture.
5. How ready are we to respond to a cybersecurity incident? How will a data security incident affect your business continuity? By assessing the risk and allocating adequate resources to protect your data, and recover it in the event of disaster, your museum can build its organizational resilience.
The Evolution of Cyber Threats and Cybersecurity
The WannaCry ransomware attack in May 2017 targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payment in the Bitcoin cryptocurrency. The attack was stopped by application of emergency patches released by Microsoft, and the discovery of a kill switch that prevented further spread from infected computers. The potential for Bitcoin to enable even more extensive cybercrime is difficult to assess, but appears likely.
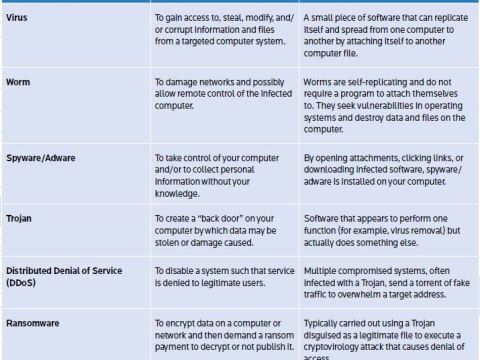
Six Types of Cyber Threats
Malware is hostile or intrusive software designed to do something sinister to your computer or network. It varies in its goal, the way it spreads, the damage it causes, and the level of risk it poses. The table below explains the six types of malware.
In addition, quantum computing capability is maturing, which is both exciting and scary. Harnessing the power of atoms and molecules to perform memory and processing tasks, quantum computers have the potential to perform calculations significantly faster than any silicon-based computer. While this unparalleled speed could help find a cure for cancer, it may also render ineffective current cryptography methods that are based on factoring ridiculously large prime numbers.
The incentives and capability to conduct malicious activity in cyberspace will doubtless increase as museums rely on the convenience, accessibility, and speed of the internet and cloud computing to store and communicate high-value or sensitive information. However, this is no reason to eschew the functionality and convenience of new technologies and devices. Rather, this is an opportunity to embrace, with open arms and eyes, the evolving digital landscape to create a living cybersecurity strategy.
Creating a fit-for-purpose cybersecurity strategy influenced by your museum’s risk appetite, business plans, and goals is not as hard as it might seem. The key to shaping such a strategy is open, pragmatic, and respectful dialogue between technology and business representatives.
Wendy Pryor is the head of technology strategy and delivery at Museums Victoria in Melbourne, Australia.







Comments